Okta: The Identity Layer of the Internet
I. Introduction & Episode Framing
Picture this: It's 2009, the depths of the financial crisis. A Salesforce executive with a newborn daughter and a fresh Type 1 diabetes diagnosis walks into his wife's home office. "I'm thinking about leaving to start a company," he says. She nearly throws him out of the house. That executive was Todd McKinnon, and the company he'd create—Okta—would become the $16 billion guardian of digital identity for thousands of enterprises worldwide.
We've all been there: Post-it notes with passwords stuck to monitors, the IT help desk on speed dial for yet another password reset, juggling dozens of login credentials across work applications. This universal pain point—multiplied across millions of employees and billions of customer interactions—created one of the most critical infrastructure opportunities of the cloud era. How did two Salesforce executives recognize this moment and build what would become the identity layer for the internet?
Okta isn't just another enterprise software company. It's the American identity and access management powerhouse that emerged from a simple observation: as businesses rushed to the cloud, their identity systems remained stuck in the basement server room. The company now processes billions of authentications monthly, protecting everyone from FedEx delivery drivers to Nasdaq traders, from JetBlue passengers checking in to millions of customers shopping online.
The journey from a failed network monitoring startup called "Saasure" to becoming the de facto identity platform for the Fortune 500 reveals profound lessons about timing markets, surviving near-death experiences, and building mission-critical infrastructure during a technological revolution. This is the story of how McKinnon and his co-founder Frederic Kerrest didn't just ride the cloud wave—they built the security gates that made enterprises feel safe enough to surf it.
As we dive into this epic tale, we'll explore three major themes that define Okta's trajectory: First, the art of category creation—how do you convince companies they need something they don't know exists? Second, the platform paradox—why identity became the ultimate sticky product in enterprise software. And third, the trust equation—what happens when a security company itself gets breached, and how do you rebuild confidence when you are the confidence layer?
From the pre-cloud dark ages of Active Directory to the $6.5 billion Auth0 acquisition, from IPO triumph to security incident crisis management, this is the definitive story of how Okta became the identity layer of the internet. Along the way, we'll uncover why Microsoft couldn't kill them, how they turned developers into evangelists, and whether they can truly become the "Salesforce of identity" in an AI-powered, passwordless future.
II. The Pre-History: Identity Management Before the Cloud
Walk into any enterprise IT department circa 2007, and you'd find yourself in a fortress of servers humming away in climate-controlled rooms. The crown jewel of this kingdom was Microsoft's Active Directory, released first with Windows 2000 Server and by then the undisputed ruler of enterprise identity management. Active Directory used Lightweight Directory Access Protocol (LDAP) versions 2 and 3, providing what seemed like a complete solution: authenticating and authorizing all users and computers in a Windows domain-type network, assigning and enforcing security policies.
But beneath this seemingly orderly surface, a storm was brewing. IT administrators spent their days wrestling with password resets—studies showed that 30-50% of help desk calls were password-related, costing enterprises an average of $70 per reset. Multiply that by thousands of employees, and you're looking at millions in lost productivity. Meanwhile, employees had developed their own shadow IT systems: Excel spreadsheets with passwords, Post-it notes on monitors, and the universal password "Company123!" that everyone knew but no one admitted to using.
The traditional identity architecture was built for a different era—one where employees sat at assigned desks, logged into company-owned computers, and accessed applications running on servers down the hall. Directory services, such as Active Directory, stored user and account information, and security information like passwords, but they were designed for a perimeter-based security model. You were either inside the castle walls or outside them. There was no middle ground.
Then came the cloud explosion of 2005-2008, and everything changed. Salesforce.com was growing at 75% annually. Google Apps (later G Suite) launched in 2006. Amazon Web Services introduced EC2 in 2006. Suddenly, critical business applications were running not in the basement but in data centers thousands of miles away. Google (PaaS), Amazon (PaaS and IaaS) and Salesforce (SaaS) represented a fundamental shift in how enterprises consumed technology.
The identity crisis this created was immediate and profound. In cloud computing, the fundamental problem is that multiple organizations are now managing the identity and access management to resources, which can greatly complicate the process. For example, imagine having to provide the same user on dozens—or hundreds—of different cloud services. Each SaaS application wanted its own username and password. IT departments couldn't extend Active Directory to these cloud services. Creating a local identity for each of the SaaS applications makes it very difficult to keep track of all the people who have access, which may result in leavers retaining access to such applications.
The problems compounded with the rise of bring-your-own-device (BYOD) policies. The iPhone launched in 2007, and suddenly employees expected to access corporate email and applications from personal devices. The neat boundaries of the corporate network dissolved. How do you enforce Active Directory group policies on an employee's personal iPad accessing Salesforce from a coffee shop?
Microsoft, Oracle, and IBM—the traditional enterprise software giants—were caught flat-footed. Their identity solutions were built for the on-premise world. Microsoft's Active Directory Federation Services (ADFS) wouldn't arrive until Windows Server 2008, and even then, it was complex to implement and maintain. These vendors were trying to extend on-premise solutions to the cloud rather than reimagining identity for a cloud-first world.
Meanwhile, security breaches were making headlines with increasing frequency. The TJX breach in 2007 exposed 94 million credit cards. Heartland Payment Systems in 2008 affected 130 million cards. Each breach investigation revealed the same pattern: compromised credentials, weak authentication, and the inability to track who had access to what across sprawling IT environments.
By 2008, the perfect storm had formed. Enterprises were adopting cloud applications at breakneck speed but had no coherent way to manage identity across them. In addition to standard identity issues plaguing enterprises, such as password fatigue and managing a distributed workforce, they faced cloud-specific IAM challenges. Shadow IT was rampant—employees were signing up for cloud services with corporate credit cards, bypassing IT entirely. Password sprawl meant the average knowledge worker was juggling 20-30 different logins. And CIOs were lying awake at night, knowing that terminated employees probably still had access to critical systems somewhere in their cloud sprawl.
This was the world Todd McKinnon and Frederic Kerrest saw from their perch at Salesforce in 2008. They didn't just see problems—they saw the fundamental architectural shift that would define the next decade of enterprise computing. The future wasn't about extending Active Directory to the cloud. It was about building identity management from the cloud, for the cloud. The stage was set for Okta's entrance.
III. The Founding Story: Leaving Salesforce to Build Okta (2009)
The PowerPoint slide that would change everything read: "Proposal to move to a new job starting a company (Why I'm not crazy)."
Todd McKinnon had put together a Google Slides presentation for his wife, titled exactly that, desperate to convince Roxanne that leaving his senior executive role at Salesforce during the worst recession since the Great Depression made sense. At the time, McKinnon had just been diagnosed with Type 1 diabetes, and he had a six-month-old daughter. Health insurance wasn't just a benefit—it was survival.
"The first difficult thing I did was tell my wife," says Todd, chuckling. "I distinctly remember coming home from work. She had our daughter in her arms and she could tell something was up. I said, 'I have to quit my job to start a company.' She'd been watching the news where Lehman Brothers was collapsing and her response was, 'Are you crazy?'"
McKinnon's argument hinged on pattern recognition and timing. His slides outlined: Cloud computing is transformative. All the great companies from Microsoft to Oracle were started during a recession. It makes things easier to start a company. He later admitted he wasn't sure he believed the recession part—he'd just read it somewhere and thought it would help convince his wife. But the cloud computing conviction? That was bone-deep.
When the urge really set in, Todd was experiencing two polar opposite life events. On the one hand, his wife had just given birth to their first child. On the other, he'd been diagnosed with Type 1 diabetes, a chronic condition he'd forever need to manage. Life suddenly felt vivid and brief. He had to act. It was 2008.
The promise McKinnon made to seal the deal wasn't about stock options or IPO dreams. Beyond being assured of their financial security, McKinnon said Roxanne wanted him to promise something else: That he'd be home for dinner every night. It was a commitment that would later shape Okta's entire culture—no-meeting Thursdays, work-from-home flexibility, a CEO without an office.
McKinnon resigned from Salesforce around Thanksgiving 2008, and then joined up with co-founder Frederic Kerrest, who'd also previously worked at Salesforce, in early 2009. Kerrest brought complementary skills—where McKinnon was the technical visionary who'd run engineering at Salesforce, Kerrest had the sales and business development chops. They'd watched the cloud revolution from inside one of its greatest success stories. Now they wanted to build the infrastructure that would enable the next thousand Salesforces.
Their first idea was a disaster. The company started out as Saasure, a network monitoring product. It didn't get traction. The founders quickly pivoted to cloud identity management and changed the name to Okta. The pivot happened fast—within months of starting. They'd been talking to potential customers about monitoring cloud applications when they kept hearing the same refrain: "We don't need monitoring. We need to know who's accessing these apps and how to control it."
Their agility and foresight led to a swift pivot towards cloud identity management, recognizing a burgeoning problem: the increasing complexity of managing user identities and access as businesses rapidly adopted cloud services and Software-as-a-Service (SaaS) applications.
The name change to Okta—a meteorological term referring to cloud cover measurement—signaled their all-in bet on the cloud. But finding believers was brutal. We started talking to VCs. We'd been really kind of, for six months we'd been out of the world in terms of financial crisis. We didn't have jobs, we weren't getting laid off, and we weren't really trying to sell anything, so we didn't see the customers. Then we started to try and raise money. We really came head on into ... venture capitalists were a little bit scared. They were freaking out.
The fundraising meetings were exercises in explaining a problem most people didn't know existed. "Identity-as-a-Service? What's that?" VCs would ask. "Active Directory works fine for us." The concept of cloud-based identity management seemed redundant to investors who couldn't envision enterprises trusting their authentication—the keys to the kingdom—to a startup.
"Okta is part of Bessemer Venture Partners' anti-portfolio—the companies this firm failed to invest in—and the fault for this one lies with your author. Back then, the conversations Todd was having with this firm at that time reflected a lot of the market. The need and go-to-market just wasn't as clear to investors as it was to Todd and Freddy. (Though, I'm glad to report that we hopefully made it up to the founders when Okta purchased Bessemer-backed Auth0 for $6.5 billion in 2021!)"
"If I can give advice to investors, it's that when you tell entrepreneurs you aren't going to invest, that conversation is going to be very vivid. It is existential for them. They are going to remember it forever," says Todd.
Despite the rejections, they scraped together initial funding. Okta secured approximately $1.2 million in seed funding, followed by a $10 million Series A round led by Andreessen Horowitz. Ben Horowitz saw what others missed—not just the technical architecture but the market timing. Salesforce had proven enterprises would trust the cloud with customer data. Now they needed to trust it with identity.
The technical decisions made in those early days would prove prescient. Instead of building their own LDAP server or trying to extend Active Directory, they built a cloud-native platform from scratch. They chose AWS as their infrastructure—a controversial decision when many enterprises still viewed Amazon as a bookstore that happened to rent servers. They architected for multi-tenancy from day one, building in the isolation and security that would later become table stakes.
"Todd recalls those early years as lonely. 'Being innovative is by definition to be lonely. You have people questioning if it's going to work, investors scrutinizing the efficiency of the payback,' he says".
But the loneliest moment came on Christmas Eve 2009. A pivotal moment was securing their first paying customer, a modest $400 order, on Christmas Eve 2009. Four hundred dollars. After a year of work, burning through savings, convincing his wife, managing diabetes, raising a baby—four hundred dollars. McKinnon later called it one of the happiest moments of his life.
Todd McKinnon: "There was pain for cloud single sign on. If you would ask them how big could this company be, they probably wouldn't have thought it would be that big. A lot of people didn't, right? A lot of people were like, oh yeah, this'll be cool to make my users happy".
What customers didn't see was the frantic building happening behind the scenes. One of our value props early on was the service would be pre-integrated to whatever they needed. It wasn't like they had to wire it together. It'd be out of the box. It would be pre-integrated to all the applications they wanted to access. We built a lot of technology to make it really easy to build these integrations, but we didn't really have any integrations built, so we would basically just get a customer's like, what apps do you have? All right, those are the ones we're building.
The "fake it till you make it" approach extended to their entire go-to-market. They'd promise integrations that didn't exist, then build them overnight. They'd demo features that were mockups in Balsamiq, then code them before the contract was signed. Every customer meeting was simultaneously a sales pitch and a product roadmap session.
McKinnon told Business Insider that when he left Salesforce.com, CEO Marc Benioff was angry. McKinnon asked Benioff for funding to start his company, and Benioff refused. At the time, McKinnon couldn't understand why. Now that he has his own company, he has gained a better understanding. When people leave Okta, he doesn't like it and takes it personally.
The rejection from Benioff stung, but it also freed them. They weren't building Salesforce 2.0 or an add-on to someone else's platform. They were creating an entirely new category: Identity-as-a-Service. In 2009, that category had exactly one company in it. The question was whether it would grow to two, or two thousand.
As 2009 turned to 2010, Okta had survived birth. They had a product, a handful of customers, and just enough funding to keep going. "We weren't the new kid on the block anymore, but hadn't been around long enough to get enterprise motion," said McKinnon. "We hunkered down and really wanted to get through the year". The real test—finding product-market fit and building an enterprise sales motion—was just beginning.
IV. The Early Years: Finding Product-Market Fit (2009-2015)
The year 2011 nearly killed Okta.
"We weren't the new kid on the block anymore, but hadn't been around long enough to get enterprise motion," McKinnon recalled. The company had raised money from Andreessen Horowitz and Floodgate, so expectations were rising, but they didn't have many big clients. McKinnon's modest goal: close the year with 50 customers. Just 50.
Hiring was brutal. Venture money was flooding into hot consumer companies like Foursquare, Instagram, and Snapchat. Who wanted to join an enterprise identity startup when you could work on the next viral app? "We hunkered down and really wanted to get through the year," McKinnon said. The company's survival hinged on Khosla Ventures stepping in to lead a $16.5 million Series B in August 2011, providing crucial runway.
But something remarkable happened in those lean years: Okta discovered its soul. The company's initial product was a single sign-on (SSO) service that allowed users to access various cloud applications with one set of credentials, simplifying authentication and improving security. This wasn't just technology—it was liberation from password hell. The single sign-on service allowed users to log into systems like Gmail, Workday, Salesforce and Slack with one login.
The early customer acquisition strategy was guerrilla warfare meets enterprise sales. They'd identify companies using multiple SaaS applications—an easy task since most proudly displayed customer logos on their websites. Then they'd cold-call IT departments with a simple pitch: "How many passwords are your employees managing? What if they only needed one?"
The product development philosophy during these years could be summarized as "say yes, then figure it out." One of our value props early on was the service would be pre-integrated to whatever they needed. It wasn't like they had to wire it together. It'd be out of the box. It would be pre-integrated to all the applications they wanted to access. We built a lot of technology to make it really easy to build these integrations, but we didn't really have any integrations built, so we would basically just get a customer's like, what apps do you have? All right, those are the ones we're building.
This approach led to the creation of what would become Okta's moat: the Application Network. The company expanded its product offerings to include Multi-Factor Authentication (MFA), Lifecycle Management, and Universal Directory. By 2012, they had built integrations with hundreds of applications. Each new integration made the platform more valuable for the next customer. Network effects in enterprise software—a beautiful thing when you can achieve it.
The cultural foundations laid during these years would define Okta for the next decade. Customer success obsession wasn't just a slogan—it was survival. Every customer was precious. Lose one, and you might not make payroll. This scarcity mindset created an intensity around customer satisfaction that most enterprise companies only dream about.
In honor of Okta's 10-year anniversary earlier this month, here are a few ways we've evolved for, and with, our customers. In the past, we waited until customers told us that they wanted product changes or that their needs were evolving. This reactive approach to product development is common and not necessarily ineffective, but it can leave users waiting to have their needs met. What a decade of listening actively to our customers has provided us with is the opportunity to build products for them in a more intentional, proactive way.
The beta program approach that emerged during this period became a signature Okta strategy. Okta selects a small number of customers for early testing of features in a Beta release. Customers participating in a Beta program agree to provide feedback that is required for maturing the feature. Rather than building in isolation, they'd work hand-in-hand with early adopters, incorporating feedback rapidly. Once beta feedback is incorporated into a product, we introduce the feature as Early Access to get the new feature in front of more customers. We want our customers to feel empowered to access what they need, so we recently introduced a self-service tool for Early Access features. This lets our customers turn on and off these features whenever they want to.
The breakthrough moment came in 2015 with the Series F round: In 2015, Okta secured a substantial venture capital investment of $75 million from prominent firms like Andreessen Horowitz, Greylock Partners, and Sequoia Capital. This funding valued the company at approximately $1.2 billion. Okta had become a unicorn.
But the real validation wasn't the valuation—it was who was buying. Fortune 500 companies were adopting Okta. These weren't early-adopter startups willing to take risks. These were conservative enterprises betting their security on a six-year-old company. Names like Adobe, Western Union, and Pitney Bowes appeared on the customer roster.
The enterprise sales motion that emerged was sophisticated yet human. Rather than selling fear ("You'll get hacked without us!"), Okta sold productivity and empowerment. They calculated the ROI of password resets, the productivity gains from faster app access, the reduced help desk tickets. CFOs loved the math. CIOs loved the simplicity. Employees loved not juggling 30 passwords.
By 2015, Okta had also figured out its market positioning against Microsoft, its most formidable competitor. Rather than compete head-on, they embraced coexistence. "We make Office 365 better," they'd say. "We're Switzerland—we work with everyone." This neutral positioning would prove crucial as enterprises adopted best-of-breed solutions from multiple vendors.
The company culture evolved but retained its startup intensity. McKinnon and Kerrest maintained their commitment to transparency, holding weekly all-hands meetings even as the company grew past 500 employees. The "no offices for executives" policy remained. Engineers got their meeting-free Thursdays. The promise to be home for dinner? Still sacred.
But perhaps the most important development during these years was the realization of what Okta really was. It wasn't just a single sign-on company. It wasn't just a security company. It was becoming the identity layer of the internet—the connecting tissue that would allow the entire SaaS revolution to function securely at scale.
Okta correctly anticipated the massive shift to cloud computing and positioned itself early as the neutral, independent identity layer needed for businesses adopting diverse cloud applications. This foresight was fundamental to its initial and sustained growth. By the end of 2015, the company had grown from that $400 Christmas Eve order to serving thousands of customers and managing millions of identities.
The path from zero to unicorn had been brutal. But Okta had found product-market fit, built a world-class enterprise sales machine, and established itself as the trusted identity partner for the cloud era. The foundation was set. Next stop: Wall Street.
V. The IPO Journey and Going Public (2016-2017)
The morning of April 7, 2017, marked a defining moment in enterprise software history. Okta's stock opened at $23.60, immediately jumping 38% above its IPO price of $17 per share. While it's a good omen for its performance in the stock market, it also means the company could have sold its shares for more than $17 — and raised more money. But it was exciting for Okta to reach this milestone, with CEO Todd McKinnon saying that they see this moment as a "step on the journey." McKinnon said that like with many startups, a lot of their employees took lower salaries because they believed their equity compensation would be worth something eventually. Some employees had been at the company for the full eight years and "they have to have a chance to sell that at some point." Okta closed the day with a market cap of $2.1 billion, above the $1.2 billion valuation at which they had previously raised capital.
The road to this moment had been carefully orchestrated. Okta's IPO will value the company at $1.5 billion, after the company sold shares at the top end of its range. Okta, a developer of security and identity management software in the cloud, is raising $187 million in an IPO for a market value of $1.5 billion, after pricing its offering at the top end of the expected range. Shares will start trading on Friday. The company, co-founded and run by former Salesforce executive Todd McKinnon, said Thursday afternoon that it sold 11 million shares for $17 apiece. The stock is set to debut on Friday on Nasdaq under the ticker OKTA.
The financial metrics that got them there told a compelling story: Revenue of $160 million in fiscal 2017, up 86% from roughly $86 million in 2016. Gross profit (before sales, admin and R&D expenses) of about $104 million in 2017, up from about $50 million in 2016. Net loss of about $84 million in 2017, compared to $76 million in 2016. In the ramp up to the IPO, Okta cranked up its sales and marketing expense to about $119 million in 2017 from about $78 million in 2016.
The timing was perfect. Technology companies are hitting the public markets again after a dreadfully slow 2016, which saw the fewest venture-backed offerings in seven years. Social media company Snap and software developer MuleSoft both priced above their expected range and then popped on their first day of trading. AppDynamics was acquired by Cisco before it could go public -- and at a much higher price than where it was set to trade. Okta is the fifth venture-backed IPO in recent weeks. Snap opened up the "window" and then MuleSoft, Alteryx and Elevate Credit followed suit. Yext is expected to debut next week.
The ownership structure at IPO revealed the venture firms that had backed the vision: Sequoia Capital is Okta's biggest investor with a 19 percent stake after the offering, followed by Andreessen Horowitz at 17 percent, Greylock Partners at 15 percent and Khosla Ventures at 7.1 percent. McKinnon owns 9.1 percent. More precisely, Venture capitalists poured about $230 million into the company. Sequoia owned the largest stake prior to the IPO, with 21.2 percent.
Sequoia partner Pat Grady's blog post captured the moment: "They not only understood this – they bet their careers on it, recruited a supremely talented team, and chose a few partners – Sequoia included – to join them in building that foundation".
McKinnon's perspective on the IPO was pragmatic rather than triumphant. An IPO was an "inevitable" step for the technology company, McKinnon told CNBC's "Squawk Box" on Friday. "The first time you take venture funding, going public is inevitable and we felt the timing was right and this was a good environment," McKinnon said.
But the real reason for going public went deeper than market timing. It was about the employees—those early believers who'd taken below-market salaries in exchange for equity, who'd worked nights and weekends building integrations, who'd weathered the tough years of 2011 when the company nearly ran out of money. "The real reason we went public is because I felt like the employees … needed a good way to get that return. I felt it was time for those employees to cash in their stock," McKinnon said.
The metrics underlying the IPO told the story of a company that had found its rhythm. They had over 4,000 customers, including marquee names like JetBlue, Nordstrom, and Rotary International. The net dollar retention rate exceeded 120%, meaning existing customers were spending significantly more each year. The land-and-expand model was working perfectly.
So how much would an investor have if they invested $1,000 in Okta's IPO? An investor could have purchased 58 Okta shares for $986. That investment will have grown to $7,306 as of this writing, yielding more than seven times the original investment.
The roadshow had been grueling—two weeks of back-to-back meetings with institutional investors, repeating the same pitch dozens of times. McKinnon and Kerrest had refined their story to its essence: Identity was becoming the new perimeter in enterprise security. As companies adopted cloud applications, traditional firewall-based security became obsolete. Identity was the only constant across all applications, devices, and locations.
The underwriters—Goldman Sachs, J.P. Morgan, and Allen & Company—had initially suggested a range of $12-14 per share. But demand was strong. They raised it to $15-17, then priced at the top of the range. The San Francisco-based company priced its offering at $17 a share, on the high end of the expected range of $15 a share to $17 a share. The 11-million-share offering will raise about $187 million for Okta, not counting an over-allotment.
The IPO prospectus revealed fascinating details about the business model. Customer acquisition costs were high—often taking 18-24 months to recover—but the lifetime value of customers was extraordinary. Large enterprises rarely switched identity providers once implemented. The switching costs were simply too high, the integration too deep. This created a moat that would only strengthen over time.
Wall Street's reaction was telling. We'll see if investors bite, just like they liked did for the first enterprise tech IPO this year, MuleSoft. Shares of MuleSoft popped 50% opening day and have stayed well above its $17 opening price ever since. The comparison to MuleSoft was apt—both were infrastructure plays for the cloud era, both had strong revenue growth despite losses, both represented bets on the continued migration to cloud computing.
The IPO also marked a cultural milestone for Silicon Valley. After years of consumer internet companies dominating the IPO landscape—Facebook, Twitter, Snap—enterprise software was back. Okta's successful debut signaled that investors were hungry for B2B SaaS companies with predictable revenue models and clear paths to profitability.
Behind the scenes, the IPO preparation had been intense. The company had hired its first CFO, Bill Losch, specifically to guide them through the process. They'd implemented more rigorous financial controls, formalized their board governance, and built out their investor relations function. The transformation from startup to public company had been happening for months before the first trade.
The competitive dynamics at IPO were complex. Microsoft's Azure Active Directory was gaining traction. Ping Identity remained a formidable competitor. New entrants like Auth0 (which Okta would later acquire) and Duo Security were attacking from different angles. But Okta's neutral positioning—working with all cloud providers rather than favoring one—gave them unique advantages.
The IPO proceeds would fuel the next phase of growth. The company planned to invest heavily in R&D to expand beyond single sign-on into adjacent areas like privileged access management and identity governance. They would accelerate international expansion, particularly in Europe and Asia. And they would continue building out their partner ecosystem, recognizing that channel sales would become increasingly important.
As trading closed on that first day, with the stock settling at $23.51, McKinnon and Kerrest gathered the team for a celebration. But McKinnon's speech was forward-looking rather than retrospective. "This is day one," he told employees. "We're 1% done with our mission." The public markets would bring new scrutiny, quarterly earnings pressure, and activist investors. But they would also bring currency for acquisitions, credibility with enterprise customers, and the validation that comes with being a public company.
The journey from two guys in a borrowed Jawbone office to a $2.1 billion public company had taken eight years. The IPO wasn't the destination—it was simply fuel for the next stage of the journey. As McKinnon had said in the prospectus's founder letter: "We believe we're still in the early innings of a massive shift to cloud computing, and identity is at the center of it all."
VI. Scaling the Platform: From SSO to Identity Cloud (2017-2020)
The milestone came quietly, buried in a CNBC interview on January 24, 2019: Okta now has more than 100 million registered users, a major milestone for the 10-year-old software company, Okta co-founder and CEO Todd McKinnon confirmed to CNBC in an exclusive "Mad Money" interview. "We're changing their world," McKinnon told CNBC's Jim Cramer on Thursday. In the 10 years since its founding, Okta has grown from two employees to more than 1,400; from zero customers to over 5,600; and from zero dollars in total revenue to above $392 million. The company's market cap currently sits at about $8.8 billion.
But the 100 million user milestone wasn't just a vanity metric—it represented a fundamental shift in what Okta had become. Identity and Access Management is not about maintaining a profile for every person on the planet. It's about an identity — for each employee, customer, or partner — for every organization in the world. When Okta thinks about scale and where we need to be in the future, we think about it in the 10s of billions of users. Our vision is to connect every user, application, organization, and device. From the start, we designed Okta's platform architecture to support this broad vision.
The technical architecture underpinning this growth was a marvel of modern cloud engineering. We authenticate several million users per hour. The Okta platform receives hundreds of millions of web requests per day across API calls, HTTP requests, and content delivery network (CDN) requests and allows customers to exceed default rate limits by 5x to 1000x when necessary. This wasn't just scale—it was hyperscale, the kind that few enterprise software companies ever achieve.
The post-IPO years had transformed Okta from a single sign-on vendor into something much larger: a comprehensive identity cloud. The product expansion during this period was relentless. Beyond the core SSO service, they'd built Multi-Factor Authentication that could handle everything from SMS to biometrics. Lifecycle Management that automated user provisioning and deprovisioning. Universal Directory that became the cloud-based system of record for user profiles. API Access Management that secured the growing world of microservices.
Each product expansion opened new markets. Recognizing that identity wasn't just an internal IT problem, Okta strategically expanded its platform to manage customer identities (CIAM). This significantly broadened its Total Addressable Market (TAM) and revenue streams. Suddenly, Okta wasn't just helping employees log into Salesforce—they were powering customer authentication for major consumer brands, managing identities for millions of end users shopping online or streaming content.
The competitive landscape during these years was fascinating. Microsoft's Azure Active Directory was gaining serious traction, bundled with Office 365 and Azure. Microsoft's Active Directory is their IAM product on Azure. Azure is a fast growing cloud platform and their ability to bundle an identity product with it makes it one to watch, since many businesses are already using other parts of their cloud offerings. While it one of the biggest competitors on management's radar, Active Directory is tied with Azure, so it's less attractive to customers not already on Azure (AWS, GCP), and less attractive to those that want to use multi-cloud.
But Okta's neutral positioning proved to be their superpower. Okta correctly anticipated the massive shift to cloud computing and positioned itself early as the neutral, independent identity layer needed for businesses adopting diverse cloud applications. This foresight was fundamental to its initial and sustained growth. They weren't trying to lock customers into a single ecosystem. They were the Switzerland of identity, working equally well with Microsoft, Google, Amazon, and everyone else.
The customer wins during this period read like a Fortune 500 directory. JetBlue using Okta to secure employee and customer identities across their entire operation. Autodesk, a leader in the design software space, selected Okta's identity cloud to centralize access management for its customers. Another important win for Okta was with a European film and television studio and distributor that has over eight million subscribers. Okta is optimistic that its offerings will support peak website traffic of up to 90,000 connections per minute during large sporting events, including soccer games.
The international expansion accelerated dramatically. International expansion comes at an ideal time for Okta, as demand for the company's enterprise identity management solution has grown significantly worldwide. Okta's customer count increased well over 100 percent since this time last year, and includes the addition of global Fortune 500 companies like MGM Resorts International and European-based organizations like London Gatwick Airport.
The architecture decisions made during this scaling phase would prove critical. Beyond Okta's proprietary cell architecture, we've built extreme redundancy at each layer of the technology stack. Even if a SaaS, PaaS, or IaaS offering used by Okta goes down, Okta remains available for its customers. This strategy extends to redundant monitoring and alerting across our infrastructure. The totality of this approach has enabled Okta to remain on and functional when entire AWS availability zones or systems go offline.
This zero-downtime architecture wasn't just marketing speak. Okta's service exceeds industry standards for cloud security, including completion of the SOC 2 Type II audit across all five trust principles. The company's zero-downtime architecture is 100 percent multitenant, stateless and extremely redundant. Okta's Amazon Web Services footprint spans eight availability zones and two geographic regions, and the service has maintained perfect availability for the past 16 months.
The business model evolution was equally impressive. One of the key drivers of Okta's incredible returns is its revenue growth. It increased sales from $257 million in fiscal 2018 to $399 million in fiscal 2019 and $586 million in fiscal 2020. Okta is focused on growing its base of large enterprise customers. Okta now has 1,467 customers with an annual contract value (ACV) of over $100,000, good for year-over-year growth of 41%.
But perhaps the most interesting development was how Okta became a platform for observing broader technology trends. Their annual "Businesses at Work" report became must-read material for understanding enterprise software adoption. This year, video conferencing favorite Zoom appeared on the list for the first time, in 9th position. One of the most interesting findings of the year, Zoom is the only app this year to show up on both the most popular and fastest growing apps. And Slack took a step up in the rankings, measured by both number of customers and active users.
The data advantage this created was profound. To create all our Businesses @ Work reports, we anonymize Okta customer data from our network of thousands of companies, applications, and IT infrastructure integrations, and millions of daily authentications and verifications from countries around the world. Our customers and their employees, contractors, partners, and customers use Okta to log in to devices, apps and services, and leverage security features to protect their sensitive data. Our customers span every major industry and vary in size, from small businesses to enterprises with hundreds of thousands of employees or millions of customers.
This network effect created a virtuous cycle. More customers meant more data. More data meant better threat detection. Better threat detection meant a more secure platform. A more secure platform attracted more customers. By 2020, Okta had become not just an identity provider but the identity intelligence network for the enterprise.
The cultural evolution during these years was equally important. The company had grown from roughly 500 employees at IPO to over 2,000 by 2020, but maintained its startup intensity. The weekly all-hands meetings continued. The no-office policy for executives remained. But now they were operating at a scale that required new levels of operational excellence.
The market recognized this transformation. Okta's stock climbed to a new 52-week high of $80.64 in Thursday's trading session, closing up 1.35 percent at $79.33 a share. An investor could have purchased 58 Okta shares for $986. That investment will have grown to $7,306 as of this writing, yielding more than seven times the original investment.
By the end of 2020, Okta had transformed from a single sign-on vendor into the comprehensive identity platform for the cloud era. They were processing billions of authentications, securing millions of identities, and had become mission-critical infrastructure for thousands of enterprises. The foundation was set for their boldest move yet—a $6.5 billion acquisition that would reshape the identity landscape forever.
VII. The Auth0 Mega-Deal: Doubling Down on Developers (2021)
The PowerPoint slide that Todd McKinnon presented to his board on March 3, 2021, contained a single, staggering number: $6.5 billion.
The acquisition announcement sent shockwaves through Silicon Valley. When Okta announced that it was acquiring Auth0 yesterday for $6.5 billion, the deal raised eyebrows. After all, it's a substantial amount of money. The company had a valuation of $1.92 billion when it raised $120 million led by Salesforce Ventures last July. In less than eight months, Auth0's valuation had jumped from $1.9 billion to $6.5 billion—a 3.5X increase that would make early investors' heads spin.
But the story behind this mega-deal wasn't about a sudden decision or inflated valuations. It was eight years in the making, a tale of persistence, vision, and the recognition that identity's future belonged to developers.
The first meeting happened in 2013, when Auth0 was barely a company. "When Okta CEO Todd McKinnon and I first had a conversation in 2013, we were a tiny company with a handful of employees and there were lots of things we hadn't figured out," recalled Eugenio Pace, Auth0's CEO and co-founder. McKinnon had already identified Auth0 as strategic. Even then, with Auth0 having just a handful of employees, McKinnon saw the future: developers would become the kingmakers of enterprise software.
The courtship that followed was remarkable for its persistence. In 2015, fresh off a funding round that bestowed upon Okta coveted, billion-dollar "unicorn" status, McKinnon and Eric Berg, Okta's then–head of product, invited Jon Gelsey, who had taken over as Auth0's CEO a year earlier, and Pace, then Auth0's chief customer officer, to lunch. McKinnon flew to Seattle, took them to a beef barbecue restaurant, and made his pitch. But even beef barbecue was not enough to sell him on Okta's vision of a joint future. "I have to confess that I also had a bit of a bias against mergers and acquisitions because in my previous life I've seen them being failures—they fall apart," Pace tells Fortune, citing a string of multibillion-dollar flops—from aQuantive to Nokia—that befell his longtime employer, Microsoft.
McKinnon's frustration was palpable. "The first time I was like, 'Oh, it's really early. It probably doesn't matter'" the former Salesforce exec says of the 2013 rejection. The second time, "I was more frustrated." But McKinnon—a CrossFit fanatic—isn't one to call it quits. Even after buying an Auth0-alternative, Stormpath, in March 2017, a month before taking Okta public, McKinnon continued to dwell on the one that got away.
The strategic rationale for the deal was compelling. The two companies actually offer complementary platforms, since only 25% of Okta's revenue comes from the customer identity market, which is one of the two markets that make up the identity and access management industry. So while Okta mostly focuses on the workforce identity market, Auth0 focuses on the customer identity market. Even while considering the two different customer identity platforms, Okta's tech is more of a pre-built solution and Auth0 is built ground-up for developers. In addition, Auth0 has an international customer base while Okta's audience is concentrated in the US.
"I started my career as a developer," McKinnon added. "Over the years, I've seen developers become more important than ever. They are the ones building every experience on the internet." This wasn't just rhetoric—it was recognition of a fundamental shift in how software was bought and sold. Auth0 was built by developers for developers. Application builders around the world are loyal to Auth0 for its extensibility, ease of use, scope of documentation, and developer-friendly experience.
The numbers behind Auth0 were impressive. Auth0 will operate as an independent company inside Okta and will be accretive in a number of ways once the deal closes, as Auth0 expects more than $200 million annual recurring revenue over the next year. As an easily implementable and customizable authentication and authorization solution, it secures more than 2.5 billion logins per month and has 7,000 customers. The company focuses on customer identity management, which Okta has identified as a $25 billion market and makes up about half of Okta's business, with employee identity management making up the other half.
The valuation math, while eye-popping, made strategic sense. Our valuation was less than $2 billion six months ago. For someone who invested in our Series F round in July, this is a 3.5X increase in six months. I would call that a pretty good deal. And for our very early investors, this is more than a 200X return. When buying companies, acquiring entities nearly always pay a premium. Just ask Salesforce about its Slack deal. So to see the $6.5 billion price tag come in above our estimates is not a surprise.
The all-stock structure of the deal was critical. It is also an all-stock deal. That was a little bit by design. The reason we're doing this is because of growth. We can grow faster, better, and do more in the world together with Okta, rather than being separate. My bet is the Okta stock that we're now a part of is going to grow much faster than separate stocks on their own. And because we hold Okta stock, we're able to get that upside. If this was a cash acquisition made by a big company, I would have some reservations. We're not cashing out.
The market's initial reaction was brutal. Still unprofitable, the company's share price tanked 20% on the news as investors worried about overpayment on a premium price tag. There has also been some cause for concern on the guidance Okta gave in fiscal 2022 with a forecasted loss of 44 to 49 cents per share versus the estimates of a four-cent profit. Thus, a merger despite forecasted losses has left investors feeling slightly uneasy.
But McKinnon and Pace saw what the market initially missed. "What had become super clear is how distinct and complementary we were, even though we've been trying to build this developer stuff," McKinnon says. The combined entities could fill in a soup-to-nuts kind of identity offering. Ben Horowitz, an early Okta investor and board member and namesake cofounder of the venture capital firm Andreessen Horowitz, agrees, saying the combo will "bring the best of both worlds" to customers.
The vision extended beyond mere financial engineering. "Together, Okta and Auth0 address a broad set of identity use cases and the acquisition will accelerate the companies' shared vision of enabling everyone to safely use any technology, shaping the future of identity on the internet". With continued global market tailwinds of cloud and hybrid IT, digital transformation, and zero-trust security, an identity platform has become one of the most critical technology investments an organization will make. These trends have accelerated over the past year as companies of all sizes and across every industry had to quickly pivot to deliver engaging customer experiences online.
The integration strategy was carefully crafted to preserve what made each company special. Auth0 will operate as an independent business unit inside of Okta, and both platforms will be supported, invested in, and integrated over time — becoming more compelling together. Auth0 will operate as an independent business unit within Okta, led by Auth0 Chief Executive Officer and Co-Founder Eugenio Pace, reporting directly to Todd McKinnon, Chief Executive Officer and Co-Founder of Okta.
The cultural considerations were equally important. "The odds might not be in our favor if you look at the statistics of M&A in general. Many of those transactions don't end up well. The causes of those failures can be incompatibility in vision, in culture, in leadership — but those have not happened to us. We have more in common than that divides us — our values, our convictions for the future, etc."
For the broader identity market, the deal represented a watershed moment. The transaction will accelerate Okta's growth in the $55 billion identity market. "There are a few other [primary cloud categories], but one of those has to be identity. And for identity to rise to that status, it has to cover all the use cases," McKinnon explained. Together, we can offer our customers workforce and customer identity solutions with exceptional speed, simplicity, security, reliability and scalability. As demand in the cloud and digital securitisation sector increases around the globe, identity platforms such as the one's Okta plan offer have gone from being a luxury for some businesses to being a necessity for most businesses.
The deal officially closed on May 3, 2021. But for Eugenio Pace, the major milestone is just another marker — albeit a lucrative one — in the Auth0 journey. "It feels a little bit like starting again, as an entrepreneur and as a founder".
The financial impact was immediate. Okta is buying itself a faster growth rate. The company expects to grow 30% to 31% in the current quarter, and 29% to 30% in its current fiscal year. So Okta is not merely purchasing a large block of revenue, but a chunk of top line that is growing more quickly than the rest of its business. And when we factor in, say, $150 million of GAAP revenue for Auth0 this year, Okta reaches more than $1.2 billion in total revenue instead of its current estimate of $1.08 billion to $1.09 billion. That's material.
Industry observers recognized the transformative nature of the deal. "Credence goes to those who can help us identify one another in a digital world," said Jay Bretzmann, Program Director for Cybersecurity Products, IDC. "Okta and Auth0 provide the cloud-ready, developer-friendly tools to help in the fight. They're building the platforms and technology we'll need to take the next steps."
Looking back, the Auth0 acquisition represented more than just market consolidation. It was a bet on the future of identity itself—that developers, not IT departments, would increasingly drive technology decisions. That customer identity was as important as employee identity. That the best enterprise software companies would need to master both top-down sales and bottom-up adoption.
"Okta and Auth0 have an incredible opportunity to build the identity platform of the future," said Eugenio Pace. The $6.5 billion price tag wasn't just for Auth0's technology or customer base—it was for the chance to define what identity meant in an increasingly digital world. As McKinnon put it: "In an increasingly digital world, identity is the unifying means by which we use technology — both at work and in our personal lives."
The deal would prove to be both Okta's greatest triumph and the beginning of its most challenging chapter. But on that March day in 2021, with the announcement shocking Silicon Valley, it felt like destiny finally fulfilled—eight years of persistence paying off in a single, transformative moment.
VIII. The Security Incidents: Crisis Management and Trust (2022-2023)
The screenshots appeared on Telegram at 3:30 AM Pacific Time on March 22, 2022, like a bomb detonating in slow motion across the cybersecurity world.
Through its usual means of communication, its Telegram channel, the LAPSUS$ group had posted screenshots of what appeared to be superuser access to the Okta management console. The images showed Okta's internal Slack channels, Jira tickets, and most damning of all—access to customer support tools that could potentially compromise client systems. The hacking group's message was brazen: "BEFORE PEOPLE START ASKING: WE DID NOT ACCESS/STEAL ANY DATABASES FROM OKTA – our focus was ONLY on okta customers."
On March 22, 2022, nearly 24 hours ago, a number of screenshots were published online that were taken from a computer used by one of Okta's third-party customer support engineers. The sharing of these screenshots is embarrassing for myself and the whole Okta team, David Bradbury, Okta's Chief Security Officer, would later admit.
But the real scandal wasn't the breach itself—it was what came next. Or rather, what hadn't come for two months.
The timeline revealed the damning truth: January 20, 2022, 23:18 – Okta Security received an alert that a new factor was added to a Sitel account. March 17, 2022 – Okta received a summary report about the incident from Sitel. March 22, 2022, at 03:30 – Screenshots shared online by LAPSUS$. The breach had occurred in January. Okta had known about suspicious activity since January 20. Yet customers weren't informed until LAPSUS$ forced their hand two months later.
The initial response from Okta was a masterclass in how not to handle a security incident. The Okta service has not been breached and remains fully operational. There are no corrective actions that need to be taken by our customers, the company initially claimed. The carefully worded statement—technically true but fundamentally misleading—sparked immediate backlash.
If you're confused about Okta saying the "service has not been breached," remember that the statement is purely a legal word soup. Fact is that a third-party was breached; that breach affected Okta; failure to disclose it affected Okta's customers, security researcher Runa Sandvik posted on Twitter, capturing the industry's fury.
As pressure mounted, the truth began to emerge in painful increments. The report highlighted that there was a five-day window of time between January 16-21, 2022, where an attacker had access to a support engineer's laptop. Our investigation determined that the screenshots, which were not contained in the Sitel summary report, were taken from a Sitel support engineer's computer upon which an attacker had obtained remote access using RDP. This device was owned and managed by Sitel.
The scope of the breach expanded with each update. Initially, Okta claimed minimal impact. Then came the admission: His conclusion was that the maximum potential impact of the breach is 366 (approximately 2.5% of) customers whose Okta tenant was accessed by Sitel. For a company managing identity for 15,000 organizations, 2.5% meant hundreds of enterprises potentially compromised.
The customer revolt was swift and brutal. The cloud infrastructure and security provider Cloudflare Inc. publicly discussed dumping Okta as a vendor and published its own blog post with tips on how security teams should hunt for threats. Cloudflare's CEO Matthew Prince tweeted: "We are resetting the @Okta credentials of any employees who've changed their passwords in the last 4 months, out of abundance of caution. We've confirmed no compromise. Okta is one layer of security. Given they may have an issue we're evaluating alternatives for that layer."
Amit Yoran, chief executive of security firm Tenable Inc., wrote in a LinkedIn post on March 23rd that the breach should have been disclosed either in January or after a timely forensic analysis and stated "As a customer, all we can say is that Okta has not contacted us". The message from customers was clear: the breach was bad, but the cover-up was unforgivable.
LAPSUS$ itself seemed to revel in the chaos, engaging in a bizarre public dialogue with Okta. In what is fast becoming a bizarre back-and-forth, LAPSU$ took to Telegram to respond to Okta's assertions. Although the group doesn't dispute that support engineers are limited to the applications Bradbury listed, it does take issue with whether that access is as benign as he suggests, commenting that it's "…rather a bad security practice to store AWS keys in Slack channels", and "The potential impact to Okta customers is NOT limited, I'm pretty certain resetting passwords and MFA would result in complete compromise of many clients systems".
The investigation that followed revealed both the limited actual damage and the massive reputational carnage. As a result of the thorough investigation of our internal security experts, as well as a globally recognized cybersecurity firm whom we engaged to produce a forensic report, we are now able to conclude that the impact of the incident was significantly less than the maximum potential impact Okta initially shared on March 22, 2022. Control lasted for 25 consecutive minutes on January 21, 2022. During that limited window of time, the threat actor accessed two active customer tenants within the SuperUser application.
Twenty-five minutes. That was all the time LAPSUS$ had actual control. But the damage to trust would last far longer.
The October 2023 incident would prove even more devastating, though it started with a simple notification from BeyondTrust. In early October 2023, Okta was notified of a breach resulting in hackers stealing HTTP access tokens from Okta's support platform by BeyondTrust. Okta denied the incident for a number of weeks, but later recognized that a breach had occurred.
This time, the impact was catastrophic and the customer list read like a who's who of major corporations: Customers impacted by the Okta breach included Caesars Entertainment, MGM Resorts International, 1Password and Cloudflare. The MGM breach alone would cost the casino giant over $100 million in lost revenue as their systems were crippled for days.
The final blow came with the revelation: On November 29th, 2023, it was known that the security incident affected all Okta customers. Every. Single. Customer. The company that secured identities for thousands of enterprises had failed to secure its own support system.
McKinnon's response to the crisis revealed both accountability and anguish. I am greatly disappointed by the long period of time that transpired between our notification to Sitel and the issuance of the complete investigation report. Upon reflection, once we received the Sitel summary report we should have moved more swiftly to understand its implications.
The company scrambled to rebuild trust with what they called the "Secure Identity Commitment." The Okta Security Action Plan, which outlines Okta's short and long term steps to strengthen the security of our third-party processors with access to customer support systems. Okta is strengthening our audit procedures of our sub-processors and will confirm they comply with our new security requirements. We will require that sub-processors who provide Support Services on Okta's behalf adopt "Zero Trust" security architectures.
But the deeper questions lingered. How could a security company fail so spectacularly at security? How could they sit on breach information for months while preaching transparency? The industry consensus was damning: The breach at Okta highlights the work companies need to do to vet third-parties, contractors and their employees, said Andras Cser, VP and principal analyst of security and risk management at Forrester. This includes auditing compliance and penetration testing checks and third-party access monitoring processes. Companies also need to employ zero trust principles when assigning entitlements to subprocessor employees.
The stock market rendered its own verdict. From a peak valuation of $41.29 billion in September 2021, Okta's market cap would crater as incidents piled up and customer confidence evaporated. The company that had built its reputation on trust had learned the hardest lesson in security: trust, once broken, is nearly impossible to rebuild.
While the overall impact of the compromise has been determined to be significantly smaller than we initially scoped, we recognize the broad toll this kind of compromise can have on our customers and their trust in Okta, the company acknowledged. But recognition wasn't enough. The damage was done.
The LAPSUS$ breach and subsequent incidents marked a turning point for Okta. They were no longer the scrappy startup challenging Microsoft. They were the incumbent, the critical infrastructure, the single point of failure for thousands of organizations. And they had failed.
As one security researcher put it: "Okta's incidents prove something we've always known but rarely admitted—even security companies are vulnerable. The difference is what you do when it happens. And Okta did everything wrong."
The path forward would require not just better security, but a fundamental rebuild of customer trust. Whether Okta could achieve that while maintaining its growth trajectory remained an open question. But one thing was certain: the era of blind faith in identity providers was over.
IX. Modern Era: The Platform Strategy (2021-Present)
The transformation was nothing short of remarkable. By May 2024, Okta posted Q1 revenue growth of 19% year-over-year with record operating cash flow of $219 million and free cash flow of $214 million. For Q3 2024, revenue grew 14% year-over-year with operating cash flow of $159 million and free cash flow of $154 million. But perhaps most importantly, the company swung to profitability, reporting net income of $16 million, or 9 cents per share, during the quarter, compared with a net loss of $81 million, or 49 cents per share, in the same period last year.
The company's current scale tells the story of how far they've come from that $400 Christmas Eve order. Q4 revenue and subscription revenue grew 13% year-over-year, with remaining performance obligations (RPO) growing 25% year-over-year and current remaining performance obligations (cRPO) growing 15% year-over-year. The business now generates record operating cash flow of $286 million and free cash flow of $284 million.
McKinnon's leadership philosophy during this period remained consistent with the startup days, but adapted for scale. "Our solid Q3 results were underpinned by continued strong profitability and cash flow. The focused investments we've made in our partner ecosystem, the public sector vertical, and large customers are materializing in our business with each of these areas contributing meaningfully to top-line growth."
The product portfolio evolution during this period was equally impressive. Okta Privileged Access uses a policy framework to determine who can access privileged resources and how. The "how" can be conditions (such as "traffic must be routed via a gateway") and/or controls (such as "phishing-resistant MFA" must be used to access this server for this account). This represented a significant expansion beyond the original SSO vision.
Okta Privileged Access became generally available on December 1, 2023, marking another major platform expansion. The solution included sophisticated capabilities: Privileged account vaulting to safeguard critical accounts by securely vaulting and managing privileged credentials. Secrets management to securely store and manage sensitive information such as API keys, passwords, and encryption keys, with secrets vaulting safeguarding critical data from unauthorized access.
The Identity Governance capabilities were equally transformative. Okta protects, manages, and audits access to critical resources efficiently and effectively with Lifecycle Management, Access Governance, and Workflows. Organizations can now harness the power of unified risk signals using Governance Analyzer recommendations, improving governance decisions.
The innovation in authentication methods showed Okta's commitment to staying ahead of security trends. The company enabled organizations to leverage their native Desktop MFA feature to extend a passwordless experience to device login and broadened supported factors to include FIDO2 YubiKeys. New features include passwordless authentication, unlimited social and Okta connections, and support for custom domains.
The biometric authentication evolution was particularly notable. Biometrics are replacing traditional passwords, aligning with Zero Trust's continuous verification approach. Biometric authentication strengthens defenses against sophisticated attacks by providing secure, hard-to-replicate verification methods. The number of individuals using security keys and biometrics increased by a whopping 158 percent on a year-over-year basis.
AI integration became a key differentiator. Okta AI's capabilities are being built on Google's Vertex AI, including a new Log Investigator powered by a generative AI chatbot. If a user triggers Universal Logout, a security professional could use Log Investigator to get a natural-language summary of the events and risk factors. Workforce Identity Cloud AI capabilities—including Log Investigator, Universal Logout, policy recommendations and more—will become available in 2024.
The competitive landscape during this period remained intense but Okta maintained its position. Microsoft, Ping Identity, Okta and IBM remain atop the Magic Quadrant in 2024. Gartner said modern access management features aim to reduce attack surfaces and mitigate risks from compromised credentials. Gartner rated Ping Identity as having the most complete vision for access management, with Okta taking the silver, Microsoft taking bronze. From an execution ability standpoint, Microsoft snatched the gold, Okta took silver.
The market dynamics showed both opportunity and challenge. Due to the prevalence of companies that leverage Microsoft's Office 365 tools, it is easy for companies to purchase or add Azure AD licenses. But Okta's neutral positioning continued to resonate: Okta is a vendor-neutral cloud based identity and access solution that requires no tradeoffs between ease of use and full functionality.
The platform approach to non-human identities emerged as a crucial new frontier. Autonomous generative AI agents are under development. CSA and Astrix Research found that non-human identities pose significant security risks. With Secure SaaS Service Accounts in Okta Privileged Access, we aim to help customers protect service accounts across an organization with account takeover, vaulting, and password rotations. Security and IT teams can take control of non-federated accounts in an organization's SaaS environment and manage them as part of their broader Identity posture.
The unified platform vision crystallized during this period. Many organizations use separate tools for IAM, IGA, and PAM, but it results in silos that hamper productivity and security. Okta Privileged Access is part of Okta Workforce Identity Cloud—a unified solution for everyone, and every need. This wasn't just product consolidation—it was architectural coherence at scale.
Identity Secure Posture Management became Generally Available in Q4 2024, able to automatically remediate critical risks. Leveraging the broader Okta platform, it will be able to enforce MFA for critical roles or trigger an access certification campaign in Okta Identity Governance.
The financial performance during this period validated the platform strategy. Despite the security incidents and market challenges, the company continued to grow. The shift to profitability while maintaining double-digit growth represented a crucial inflection point—proof that Okta could balance growth with fiscal discipline.
By 2024, Okta had evolved from a single sign-on startup into the comprehensive identity platform McKinnon and Kerrest had envisioned. The journey from two guys in a borrowed office to a profitable, growing public company managing billions of authentications monthly was complete. But as McKinnon would be the first to say, they were still only 10% done with their mission.
X. Playbook: Business & Strategy Lessons
The Okta story isn't just about building a successful identity management company—it's a masterclass in category creation, platform dynamics, and navigating the treacherous waters of enterprise software. The playbook that emerges from their journey offers profound lessons for any company attempting to build mission-critical infrastructure in the cloud era.
The Power of Category Creation: Inventing Identity-as-a-Service
When McKinnon and Kerrest left Salesforce in 2009, they didn't just build a better mousetrap—they invented an entirely new category. Identity-as-a-Service didn't exist as a concept. The genius wasn't in recognizing that identity management was broken (everyone knew that), but in understanding that the solution required a fundamentally different architecture.
The category creation playbook has three essential elements. First, timing the technological shift. Okta launched just as enterprises were beginning their cloud migration in earnest. Too early, and the market wouldn't understand the need. Too late, and incumbents would have adapted. Second, simplifying the complex. They took the arcane world of SAML, OAuth, and LDAP and made it accessible through a clean, intuitive interface. Third, evangelizing relentlessly. McKinnon and Kerrest didn't just sell a product—they sold a vision of what identity could be in the cloud era.
The lesson: Don't compete in existing categories if you can create your own. But category creation requires not just vision but the patience to educate the market, often for years before widespread adoption.
Platform Dynamics: Why Identity is the Ultimate Sticky Product
Okta's platform dynamics reveal why identity became such a powerful business model. Every integration made the platform more valuable. Every customer added made the next sale easier. Every authentication strengthened the network effect.
The stickiness comes from three sources. First, the switching costs are astronomical. Once Okta becomes the authentication layer for hundreds of applications and thousands of users, ripping it out would be like performing heart surgery on a running patient. Second, the integration depth. Okta doesn't just sit on top of applications—it becomes woven into the fabric of how employees work every day. Third, the trust factor. In security, reputation is everything. Every day without a breach builds the trust moat higher.
The platform expansion strategy—from SSO to MFA to Lifecycle Management to Privileged Access—wasn't random. Each addition solved an adjacent problem for the same buyer, deepening the relationship while expanding the revenue opportunity. The Auth0 acquisition accelerated this, adding developer-focused capabilities that opened entirely new use cases.
The Acquisition Strategy: When to Buy vs. Build
Okta's acquisition history reveals a disciplined approach to M&A. The Auth0 deal at $6.5 billion was the headline-grabber, but smaller acquisitions like Stormpath and ScaleFT were equally strategic. The pattern that emerges: acquire when you need to accelerate into a new market segment or when the technology would take too long to build internally.
The Auth0 acquisition wasn't about technology—Okta could have built those capabilities. It was about developer mindshare, time to market, and acquiring a different DNA. Auth0's developer-first culture complemented Okta's IT-first approach, allowing them to serve both constituencies without internal conflict.
The integration strategy mattered as much as the acquisition strategy. Keeping Auth0 as an independent business unit preserved what made it special while allowing for gradual integration where it made sense. This avoided the cultural antibodies that kill so many acquisitions.
Enterprise Sales Excellence: Landing Fortune 500s from a Startup
How does a startup with no customers convince Fortune 500 companies to trust them with the keys to the kingdom? Okta's enterprise sales playbook offers several insights.
First, start with the innovators. Early customers like LinkedIn and Western Union weren't just buyers—they were design partners who helped shape the product. These lighthouse customers provided credibility that no amount of marketing could buy.
Second, sell business value, not technology. Rather than pitching protocols and standards, Okta calculated the ROI of password resets, the productivity gains from faster access, the reduced help desk tickets. CFOs understood this math even if they didn't understand SAML.
Third, embrace the proof of concept. Okta made it easy to try before buying, confident that once IT departments experienced the simplicity, they'd never go back to the old way. The freemium model for developers (through Auth0) extended this try-before-you-buy approach to a new audience.
Fourth, build an ecosystem, not just a customer base. The partner network—from systems integrators to resellers to technology partners—multiplied Okta's reach. The Integration Network with thousands of pre-built connectors made Okta more valuable with each addition.
Developer-first vs. IT-first: Serving Two Masters Successfully
The Auth0 acquisition forced Okta to solve one of enterprise software's hardest problems: serving both developers and IT without alienating either. These audiences have different needs, buying processes, and success metrics.
The solution was organizational and architectural. Keep the platforms separate where the use cases diverge, integrate where they overlap. Maintain distinct go-to-market motions—developer evangelism for Auth0, enterprise sales for Okta—while finding synergies in customer success and support.
The lesson extends beyond identity: modern enterprise software companies must serve multiple constituencies. The winners will be those who can maintain distinct value propositions while building on a common platform.
Managing Through Crisis: Security Incidents at a Security Company
The LAPSUS$ breach and subsequent incidents could have been company-ending events. A security company that gets breached faces an existential credibility crisis. Okta's response, while imperfect, offers lessons in crisis management.
What went wrong: The initial response was too slow, too technical, and too defensive. Waiting months to disclose, even if the actual impact was minimal, violated the cardinal rule of security: transparency builds trust, opacity destroys it.
What went right: The eventual response was comprehensive. The Secure Identity Commitment wasn't just PR—it represented real architectural and process changes. More importantly, McKinnon took personal responsibility, acknowledging the failures without excuses.
The broader lesson: In mission-critical infrastructure, trust is your real product. One incident handled poorly can undo years of reputation building. But handled well, a crisis can actually strengthen customer relationships by demonstrating commitment to continuous improvement.
The Importance of Founder-Led Leadership Through Scale
Many founders step aside as their companies scale, replaced by "professional" CEOs. McKinnon and Kerrest's continued leadership through IPO and beyond offers a different model.
The advantages of founder leadership at scale are clear in Okta's story. The consistent vision from founding through today prevented the strategy thrashing that plagues many enterprise companies. The cultural continuity—from no offices for executives to the focus on customer success—maintained startup intensity even at billions in revenue. The authentic voice in crisis, with McKinnon personally addressing security incidents, carried more weight than any hired CEO could muster.
But it required evolution. The McKinnon of 2024 isn't the same leader who started Okta in 2009. He learned to delegate operations while maintaining strategic control, to be the chief evangelist while empowering other voices, to balance founder passion with public company discipline.
The Neutral Switzerland Strategy
Perhaps Okta's most brilliant strategic decision was positioning itself as Switzerland in the identity wars. While Microsoft pushed Azure AD as part of its ecosystem, while Google integrated identity with its cloud platform, Okta remained steadfastly neutral.
This neutrality wasn't passive—it was actively cultivated. Okta invested heavily in making Office 365 work better, even as Microsoft competed with them. They integrated deeply with AWS, Google Cloud, and Azure simultaneously. They supported every SSO protocol, every MFA method, every directory service.
The strategy required discipline. There were surely moments when picking sides—going all-in on AWS, or building exclusively for Microsoft—would have been easier. But neutrality became Okta's superpower, allowing them to win customers who used multiple clouds, who wanted vendor independence, who valued flexibility over lock-in.
The Identity Intelligence Network Effect
Okta's data advantage deserves special attention. With billions of authentications flowing through their platform, they see patterns others miss. This isn't just about security—though the threat intelligence is valuable. It's about understanding how enterprises actually work.
The Businesses at Work report became must-read material not because Okta has opinions about enterprise software, but because they have data. They know which apps are gaining adoption, which authentication methods work best, which integration patterns succeed. This intelligence becomes a competitive moat that grows stronger with each customer.
The Platform Extensibility Philosophy
Unlike many enterprise software companies that try to do everything themselves, Okta embraced extensibility from day one. The Integration Network, the partner ecosystem, the APIs—all designed to make Okta the identity hub that others build around, not a walled garden.
This required restraint. There were surely features Okta could have built that they instead left to partners. But by creating a thriving ecosystem, they multiplied their value without multiplying their complexity. Every partner integration made Okta more valuable. Every developer who built on their platform became an advocate.
The playbook that emerges from Okta's journey isn't just about identity management—it's about building enduring enterprise software companies in the cloud era. Create categories rather than competing in them. Build platforms that get stronger with scale. Remain neutral in ecosystem wars. Serve multiple constituencies without compromise. Maintain founder vision while evolving leadership. And above all, remember that in mission-critical infrastructure, trust is the ultimate currency.
XI. Bear vs. Bull Case & Valuation Analysis
The investment case for Okta presents a fascinating study in contrasts. A company that has grown from zero to billions in revenue, survived security breaches that would have killed lesser companies, and positioned itself at the center of one of technology's most critical layers. Yet the stock trades well below its 2021 peaks, creating a battleground between believers and skeptics.
Bull Case: The Inevitable Identity Layer
The bulls see Okta as critically undervalued, a coiled spring ready to return to growth as the identity market explodes. Their argument rests on several powerful pillars.
First, the TAM expansion story is just beginning. The Identity And Access Management (IAM) Market size is projected to grow from USD 22.9 billion in 2024 to USD 34.3 billion by 2029 at a CAGR of 8.4% during the forecast period. The growth of the IAM market is being driven by several factors. But Okta sees an even larger opportunity—management has identified an $80 billion TAM by including adjacencies like privileged access and governance. Okta has market share of 40.94% in identity-access-management market. Okta competes with 26 competitor tools in identity-access-management category. The top alternatives for Okta identity-access-management tool are OneLogin with 44.44%, Duo Security with 3.10%, Gigya with 2.95% market share.
The platform stickiness creates compounding value. Once embedded, Okta becomes nearly impossible to rip out. The switching costs—reintegrating hundreds of applications, retraining thousands of users, rebuilding security policies—create a moat that widens over time. Net retention rates above 110% demonstrate that customers don't just stay—they expand.
The Auth0 synergies are finally materializing after a rocky integration. The combined platform now serves both IT buyers and developers, a unique position in the market. As enterprises increasingly need both workforce and customer identity solutions, Okta is the only vendor that can credibly serve both from a single platform.
Zero Trust architecture is becoming mandatory, not optional. The increasing occurrence of security breaches and identity-related frauds have created a heightened demand for robust IAM solutions. Organizations are becoming more aware of the importance of compliance management and are investing in IAM systems to meet regulatory requirements. The COVID-19 pandemic has led to a greater focus on cybersecurity, prompting organizations to increase their investments in IAM solutions.
The AI and machine identity opportunity could dwarf the human identity market. As enterprises deploy AI agents and automated systems, each needs identity and access management. Okta's early moves into non-human identity position them to capture this emerging market.
The profitability inflection changes everything. After years of growth-at-all-costs, Okta has proven it can generate cash. Record operating cash flow of $286 million and free cash flow of $284 million demonstrates the underlying unit economics are sound. As growth investments moderate, margins should expand significantly.
Bear Case: The Challenged Champion
The bears see a company facing existential threats from multiple directions, with execution challenges that management hasn't fully addressed.
The security incidents have caused lasting reputation damage. No matter how Okta spins it, a security company that gets breached repeatedly faces a credibility crisis. Enterprise buyers have long memories, and competitors never let them forget. The October 2023 incident affecting all customers was particularly damaging—how can you trust a security vendor that can't secure itself?
Microsoft's bundling threat is intensifying. Microsoft has the highest scores for overall viability, marketing execution, business model, and sales execution/pricing. With Azure AD (now Entra ID) improving rapidly and bundled with Office 365, Microsoft can offer "good enough" identity management essentially for free. For cost-conscious IT departments, free and integrated beats best-of-breed.
Growth deceleration suggests market maturation. Revenue growth has slowed from 40%+ to the mid-teens. While management blames execution issues and macro headwinds, the reality might be simpler: the easy wins are gone. Most enterprises that needed cloud identity have already chosen a solution.
Integration execution remains questionable. The Auth0 integration took longer and cost more than expected. Management changes continue, suggesting internal turmoil. The failure to reiterate long-term targets raises questions about visibility and execution capability.
Valuation remains demanding despite the correction. Even after falling from peak valuations, Okta trades at premium multiples. With growth slowing and competition intensifying, those multiples may compress further.
The identity market is getting crowded. Beyond Microsoft, companies like CyberArk, Ping Identity (now part of Thoma Bravo's portfolio), and newer entrants are all competing for the same dollars. The consolidation in the space—Thoma Bravo's acquisitions, IBM's moves—suggests returns may be diminishing.
Valuation Analysis: Finding Fair Value
With Okta stock trading at $99.28 per share, the total value of Okta stock (market capitalization) is $17.38B. This represents a significant decline from peak valuations above $40 billion in 2021, but the question remains: is this cheap or appropriately valued?
Looking at traditional metrics, the picture is mixed. Price/Sales ratio of 6.13 suggests the market still expects significant growth. For comparison, mature enterprise software companies trade at 3-4x sales, while high-growth SaaS companies can command 10x or more.
The analyst community remains cautiously optimistic but divided. Okta, Inc. has a consensus rating of Moderate Buy which is based on 21 buy ratings, 12 hold ratings and 2 sell ratings. The average price target for Okta, Inc. is $123.25. This is based on 35 Wall Streets Analysts 12-month price targets, issued in the past 3 months.
The range of price targets reveals the uncertainty: The 39 analysts that cover Okta stock have a consensus rating of "Buy" and an average price target of $121.55, which forecasts a 19.62% increase in the stock price over the next year. The lowest target is $75 and the highest is $140. This wide spread—from $75 to $140—reflects fundamental disagreements about Okta's future.
Looking at growth versus profitability, Okta is at an inflection point. The company has proven it can be profitable, but at what growth rate? If growth reaccelerates to 20%+, current valuations look reasonable. If it settles into the low teens, the multiple should compress.
The sum-of-the-parts analysis suggests hidden value. The workforce identity business alone could be worth $10-12 billion based on comparable transactions. The customer identity business (Auth0) could be worth $5-7 billion. The emerging privileged access and governance businesses add another $2-3 billion in value. This suggests a fair value range of $17-22 billion, indicating limited downside from current levels.
Risk Factors & Catalysts
The key risks facing Okta are clear but not necessarily probable. Another major security breach could be catastrophic. Microsoft could get aggressive with bundling and pricing. A recession could slow enterprise software spending. The Auth0 integration could continue to disappoint.
But the potential catalysts are equally powerful. An acceleration in cloud migration post-AI boom could drive demand. Successful new product launches in privileged access could expand TAM. International expansion could open new growth vectors. M&A activity—either as acquirer or target—could unlock value.
The Verdict: Asymmetric Opportunity
The weight of evidence suggests Okta represents an asymmetric opportunity. The downside appears limited—the company is profitable, growing double digits, and serving a critical need. The business model is sound, the competitive position defensible, and the market opportunity expanding.
The upside, however, could be substantial. If Okta executes on its platform vision, reaccelerates growth, and captures even a modest share of the expanded TAM, the stock could double from current levels. Okta, Inc. has 26.02% upside potential, based on the analysts' average price target, but this may prove conservative if the company returns to form.
The key is time horizon. Short-term traders should be cautious—the stock could remain volatile as the company works through execution challenges. But long-term investors might see today's price as an attractive entry point for a company that could define identity management for the next decade.
The bear case is real and shouldn't be dismissed. But the bull case—that Okta becomes the Switzerland of identity, the trusted neutral platform that enables the entire cloud ecosystem—remains intact. At current valuations, the market is pricing in significant execution risk. If management can execute even moderately well, the risk-reward favors the bulls.
XII. The Future: What's Next for Digital Identity
The future of digital identity extends far beyond passwords and single sign-on. As we stand on the precipice of an AI-dominated era, where machines talk to machines and digital agents operate autonomously, the very concept of identity is being revolutionized. Okta's position in this transformation—whether as leader, fast follower, or disrupted incumbent—will determine its fate over the next decade.
The Passwordless Future and Biometric Authentication
The password's death has been predicted for decades, but this time it's real. Passkeys are an alternative to passwords developed to allow a system to identify a device instead of requiring a user to recall and send a password. They allow users to associate login information with devices by using hardware keys. That means users don't have passwords that can be easily forgotten or stolen. With a passkey, computers, phones or tablets can be used along with a personal identification number or biometric authentication method. This allows users to use a mobile device to log into their accounts and eliminates the need for passwords, captchas or two-factor authentication.
The biometric revolution is accelerating beyond fingerprints and facial recognition. Gait recognition assesses the unique, identifiable way a person walks. Behavioral biometrics examines a person's behavior using a range of techniques around actions like mouse movement, typing rhythm, and interaction patterns with devices. These passive authentication methods could eliminate the login process entirely—the system knows who you are by how you interact with it.
Okta's approach to this passwordless future is pragmatic rather than revolutionary. FastPass is a phishing-resistant, passwordless authenticator under the Okta Verify application that helps mitigate the impact of phishing attacks, session theft, and unauthorized local activity. Designed for defense in depth, FastPass evaluates device context each time the user opens a protected resource and provides a user-friendly experience consistent across all major platforms and devices.
The challenge isn't technology—it's adoption. Enterprises move slowly, and legacy systems don't disappear overnight. Okta must support both passwordless pioneers and password-dependent laggards simultaneously, a complex balancing act that will define the next five years.
Decentralized Identity and Web3 Implications
The Web3 movement promises a radical reimagining of identity: self-sovereign, portable, and owned by users rather than corporations. Blockchain-based identity systems could theoretically eliminate centralized identity providers like Okta entirely. Your identity would live on a blockchain, controlled by your private keys, portable across any service.
But the reality is more nuanced. Enterprises need accountability, compliance, and recourse—things that decentralized systems struggle to provide. The more likely outcome is a hybrid model where decentralized identity supplements rather than replaces centralized systems. Okta could become the bridge between Web3 and enterprise, translating blockchain identities into enterprise-speak.
The company hasn't made major Web3 moves yet, a strategic choice that could prove either prescient or problematic. If Web3 identity remains niche, Okta's focus on practical enterprise needs looks smart. If decentralized identity goes mainstream, Okta could find itself disrupted by a new architecture it doesn't control.
AI-Powered Threat Detection and Adaptive Authentication
The real AI revolution in identity isn't chatbots—it's intelligence that operates at machine speed to detect and respond to threats. Okta AI embeds artificial intelligence features across the company's ecosystem and uses its large dataset of crowdsourced threat intelligence information and identity capabilities to power actions and provide recommendations. Okta AI can look at the best practices of millions of other developers who work in our ecosystem and offer recommendations in how to reduce friction in the login process. Which actions or workflows should you embed into your code to make the code go faster.
The future here is contextual, continuous authentication. Instead of authenticating once at login, the system constantly evaluates risk based on behavior, location, device posture, and hundreds of other signals. Suspicious activity triggers step-up authentication automatically. Normal behavior remains frictionless.
This adaptive authentication requires massive data sets and sophisticated machine learning—advantages that accrue to scale players like Okta. Every authentication through their system trains their models. Every threat detected improves their algorithms. It's a flywheel that spins faster with scale.
But AI also poses risks. Deepfakes could defeat biometric authentication. AI-powered attacks could overwhelm traditional defenses. The arms race between AI-powered attacks and AI-powered defenses will define cybersecurity for the next decade. Okta must stay ahead of this curve or risk irrelevance.
The Regulatory Landscape: GDPR, CCPA, and Identity Governance
Regulation is both tailwind and headwind for Okta. Privacy laws like GDPR and CCPA create demand for identity governance solutions—companies need to know who has access to what data and why. But they also constrain what's possible, limiting data collection and requiring complex compliance frameworks.
The regulatory trend is toward more control, not less. The EU's Digital Identity Wallet initiative aims to give citizens a single, portable digital identity for all government and many private services. China's digital identity system goes even further. The U.S. is exploring its own digital identity frameworks.
For Okta, this regulatory complexity is an opportunity. Enterprises need partners who can navigate the regulatory maze, ensuring compliance across jurisdictions. Okta's governance products position them well for this future, but execution will matter. The company that can make compliance simple wins.
The risk is regulatory capture or mandated standards that favor certain vendors. If governments mandate specific identity architectures or protocols, Okta's flexibility could become a liability. The company must engage with regulators while maintaining its vendor-neutral positioning.
M&A Opportunities and Consolidation Trends
The identity market is ripe for consolidation. Legacy on-prem IAMs like ForgeRock, IBM, Oracle, MicroFocus were slow to morph into cloud & SaaS. Microsoft adapted its widely used Active Directory to the cloud. Cloud-native IAM solutions like PingID, Okta, OneLogin, Duo, and JumpCloud emerged as disruptors. This fragmentation can't last—customers want fewer vendors, not more.
Okta could be acquirer or acquired. As acquirer, targets might include specialized players in emerging areas like IoT identity or blockchain identity. Small acquisitions that add specific capabilities make sense, following the Stormpath and ScaleFT model rather than another Auth0-sized deal.
As acquisition target, Okta would be attractive to several buyers. A private equity rollup (following Thoma Bravo's Ping Identity playbook) could unlock value through operational improvements. A strategic buyer like Salesforce, Adobe, or even Microsoft could integrate identity into their broader platforms. The $17 billion market cap is digestible for large acquirers.
The consolidation will accelerate as growth slows and multiples compress. The question isn't if but when and how. Okta's position as the independent leader gives them options—they can drive consolidation or participate in it.
Can Okta Become the "Salesforce of Identity"?
This is the billion-dollar question. Salesforce transformed CRM from a back-office function into the center of customer engagement. Can Okta similarly transform identity from a security necessity into a business enabler?
The parallels are striking. Both started with a single cloud product (CRM for Salesforce, SSO for Okta). Both expanded through acquisition and organic development into platforms. Both positioned themselves as neutral Switzerland in vendor wars. Both have charismatic founder-CEOs who evangelize their categories.
But the differences matter too. CRM directly drives revenue; identity prevents losses. Salesforce sells to lines of business; Okta primarily sells to IT. CRM has natural network effects through customer data; identity's network effects are more technical.
For Okta to become the Salesforce of identity, they need to make identity a business conversation, not just an IT conversation. Customer identity (CIAM) helps here—when identity directly affects customer experience and revenue, business leaders pay attention. The expansion into governance and privileged access broadens the conversation to risk and compliance.
The key is demonstrating business value beyond security. Can identity data improve customer experience? Can authentication patterns predict churn? Can access analytics optimize productivity? These are the questions Okta must answer to transcend its security roots.
The Technology Wildcards
Several emerging technologies could fundamentally disrupt identity management:
Quantum computing could break current encryption methods, requiring entirely new authentication architectures. Okta must prepare for a post-quantum world without over-investing before it arrives.
Edge computing pushes identity decisions closer to devices and users. As computing becomes more distributed, centralized identity providers must adapt or risk latency and availability issues.
Digital twins and metaverse environments require new identity models. How do you authenticate an avatar? Who controls identity in virtual worlds? These aren't science fiction questions—enterprises are already exploring these use cases.
Neurological authentication—using brainwaves or thoughts for authentication—sounds fantastical but is being researched. The company that cracks unobtrusive, continuous, unforgeable authentication wins the future.
Okta's Strategic Imperatives
Looking forward, Okta faces several strategic imperatives:
First, execute flawlessly on the platform integration. The Auth0 acquisition must deliver synergies. The privileged access and governance products must achieve market fit. No more unforced errors.
Second, expand internationally with purpose. The U.S. market is maturing, but international markets offer growth. This requires localization, regional partnerships, and navigating complex regulatory environments.
Third, lead in emerging identity categories. Whether it's machine identity, IoT identity, or AI agent identity, Okta must be first or fast follower. Missing a major category shift could be fatal.
Fourth, maintain technical excellence while improving usability. The product must be powerful enough for experts but simple enough for generalists. This balance is hard but essential.
Fifth, rebuild and maintain trust. Every day without a security incident rebuilds confidence. Every transparent communication strengthens relationships. Trust, once lost, takes years to rebuild.
The Verdict: Identity's Infinite Game
The future of digital identity isn't a destination—it's an infinite game where the rules constantly change. New technologies emerge. New threats appear. New regulations arise. The winner isn't who's ahead at any moment but who adapts fastest to change.
Okta is well-positioned for this infinite game. They have scale, technology, and market position. They have a clear vision and proven execution capability (recent challenges notwithstanding). Most importantly, they understand that identity is becoming more critical, not less, as our physical and digital worlds merge.
The challenges are real. Competition from Microsoft won't disappear. New architectural paradigms could disrupt their model. Execution mistakes could compound. But the opportunity is even larger. In a world where everything has an identity—every person, device, application, and AI agent—the company that manages those identities manages the digital world itself.
The next decade will determine whether Okta becomes the definitive identity platform or merely another enterprise software vendor. The pieces are in place. The market is expanding. The need is critical. The question isn't whether the identity market will grow—it's whether Okta will capture that growth or watch others claim the future they helped create.
As McKinnon might say, they're still only 10% done with their mission. The next 90% will determine whether Okta becomes the identity layer of the internet or a footnote in the history of digital transformation. Based on their track record, betting against them would be premature. But betting on them requires faith that they can execute on a vision that's ambitious even by Silicon Valley standards.
The story of Okta is far from over. In fact, it might just be beginning.
XIII. Conclusion: The Identity Layer's Manifest Destiny
Standing in Okta's San Francisco headquarters today, you can still feel the startup energy that McKinnon and Kerrest brought from that borrowed Jawbone conference room fifteen years ago. The office has no executive corner suites—true to the founding promise. Engineers still get their Thursday meeting-free zones. And somewhere, probably in a conference room overlooking the Bay, product managers are still promising customers features that don't quite exist yet, then scrambling to build them before the contract is signed.
This is the paradox of Okta: a $17 billion public company that still operates like it's fighting for survival, a profitable enterprise that remembers being two months from bankruptcy, a market leader that acts like an underdog. Perhaps this productive paranoia is what's required to own the identity layer of the internet.
The journey from zero to here reads like a Silicon Valley fairy tale—two executives leave comfortable jobs during a recession, nearly run out of money multiple times, get rejected by every VC in the Valley, then build one of the defining companies of the cloud era. But fairy tales don't include data breaches that could have ended everything, integration failures that destroyed billions in market value, or the grinding reality of competing against Microsoft's infinite resources.
What emerges from this deep dive isn't just the story of a successful technology company. It's a masterclass in market timing, category creation, and the compounding power of being right about a fundamental architectural shift. When McKinnon and Kerrest bet their careers on cloud identity in 2009, they weren't just building a company—they were betting that the entire technology industry would reorganize around cloud-first architectures. That bet, placed when most enterprises still thought the cloud was for startups and small businesses, has paid off beyond their wildest projections.
The bull case for Okta remains compelling. The identity market is expanding faster than even optimistic projections suggested. The global identity and access management market size was estimated at USD 22.9 billion in 2024 and is projected to reach USD 34.3 billion by 2029, growing at a CAGR of 8.4% from 2024 to 2029. Non-human identities could make human identity management look quaint. The company's platform approach, strengthened by the Auth0 acquisition and expansion into privileged access and governance, positions them to capture value across the entire identity stack.
But the bear case deserves equal weight. The security breaches revealed operational vulnerabilities that shook customer confidence. Microsoft's bundling power only grows stronger. New architectures—from Web3 to quantum—could obsolete current approaches. And perhaps most concerningly, growth has decelerated while competition has intensified.
The truth, as always, lies somewhere between the extremes. Okta is neither the unstoppable force its supporters claim nor the wounded giant its detractors describe. It's a company in transition—from growth to profitability, from point solution to platform, from startup to institution. These transitions are never smooth, and Okta's recent challenges reflect the difficulty of transformation at scale.
What makes Okta's story particularly relevant today is what it teaches us about building in the age of AI and digital transformation. Every company is becoming a technology company. Every interaction is becoming digital. Every asset is gaining an identity. In this context, identity isn't just about security—it's about enablement. The company that controls identity controls access, and the company that controls access controls the digital economy.
The strategic lessons from Okta's playbook transcend identity management. Category creation beats competition in existing markets. Neutral positioning can be more powerful than ecosystem lock-in. Developer-first and IT-first aren't mutually exclusive. Trust, once broken, can be rebuilt through transparency and execution. And perhaps most importantly, founder-led companies can scale beyond what traditional management theory suggests.
Looking forward, Okta faces an existential question: Can they execute on the platform vision while maintaining the agility that got them here? The privileged access and governance expansions are promising but unproven. The AI and machine identity opportunities are massive but nascent. The international expansion potential is clear but complex. Success requires threading multiple needles simultaneously—never easy, especially under public market scrutiny.
The investment implications depend on time horizon and risk tolerance. For short-term traders, Okta remains a "show me" story—prove you can reaccelerate growth, prove the platform strategy works, prove you can operate without security incidents. The stock will likely remain volatile as the market digests each quarterly report, searching for signs of execution improvement or deterioration.
For long-term investors, current valuations might represent a compelling entry point. With Okta stock trading at $99.28 per share, the total value of Okta stock (market capitalization) is $17.38B, well below the $41 billion peak. If management executes even moderately well on the platform vision, if the identity market continues expanding, if the company maintains its position as the neutral Switzerland of identity, the stock could double or triple from current levels over the next five years.
But the biggest opportunity—and risk—might be as an acquisition target. At current valuations, Okta is digestible for large strategics or private equity. A buyer could unlock value through operational improvements, deeper integration with adjacent products, or simply better execution. The question is whether McKinnon and Kerrest want to see their vision through independently or as part of something larger.
The cultural impact of Okta extends beyond financial returns. They've proven that enterprise software doesn't have to be boring, that security companies can be innovative, that you can maintain startup culture at scale. The thousands of employees who've passed through Okta have carried these lessons to other companies, spreading the gospel of customer obsession and platform thinking throughout Silicon Valley and beyond.
Perhaps most importantly, Okta has made the internet more secure and usable for millions of people who've never heard of them. Every time someone logs into work without remembering a password, every time a company prevents a breach through strong authentication, every time a developer builds identity into their application without starting from scratch, Okta's invisible hand is at work. This is the ultimate success for infrastructure companies—to become so essential that they disappear into the background, noticed only when they fail.
The verdict on Okta isn't whether they've succeeded—by any objective measure, building a profitable, growing, $17 billion company that secures millions of identities is a massive success. The question is whether this success is the peak or merely a plateau before the next climb. The answer depends on execution, market dynamics, competitive responses, and a dozen other variables that no one can perfectly predict.
What we can say with certainty is that identity will only become more critical. As physical and digital worlds merge, as AI agents proliferate, as cyber threats evolve, as regulations tighten, the need for robust, scalable, trustworthy identity management will grow. Someone will capture this value. Whether it's Okta, Microsoft, or a company that doesn't exist yet remains to be seen.
McKinnon's promise to his wife—to be home for dinner—has become part of Okta lore. It represents something deeper than work-life balance. It's about building a company that enhances life rather than consuming it, that creates value for all stakeholders rather than extracting it, that solves real problems rather than creating new ones. In an industry often criticized for its excesses and externalities, Okta represents a more sustainable model of technology company building.
As we close this deep dive into Okta's past, present, and future, one thing becomes clear: the identity wars are far from over. The battle for the identity layer of the internet will intensify as the stakes grow higher. Okta has won many battles, survived near-death experiences, and emerged as a leader. But in technology, past performance doesn't guarantee future results. The only constant is change, and the only sustainable advantage is the ability to adapt faster than your competition.
The story of Okta is ultimately a very human story—of founders who risked everything on a vision, of employees who built something from nothing, of customers who trusted a startup with their most critical systems, of investors who believed when no one else would. It's a story of persistence through rejection, resilience through crisis, and evolution through success.
Whether Okta becomes the Salesforce of identity, gets acquired by a larger player, or gets disrupted by the next paradigm shift, its impact on the technology industry is already indelible. They didn't just build a company—they created a category, defined best practices, and proved that identity deserves to be a first-class citizen in the enterprise stack.
For Todd McKinnon, Frederic Kerrest, and the thousands of Okta employees past and present, the mission continues. To secure identity so everyone can safely use any technology. To make the complex simple. To remain the trusted neutral platform in an increasingly polarized technology landscape. To be home for dinner while building the identity layer of the internet.
They're still only 10% done. The next 90% will be even harder than the first. But if the past fifteen years have taught us anything, it's that betting against Okta is a dangerous game. They've proven skeptics wrong before. They might just do it again.
The identity layer of the internet is still being written. Okta has authored several important chapters. Whether they write the conclusion remains to be seen. But one thing is certain: in a world where identity is everything, whoever controls identity controls the future. And right now, despite all the challenges and competition, Okta still holds the pen.
 Chat with this content: Summary, Analysis, News...
Chat with this content: Summary, Analysis, News...
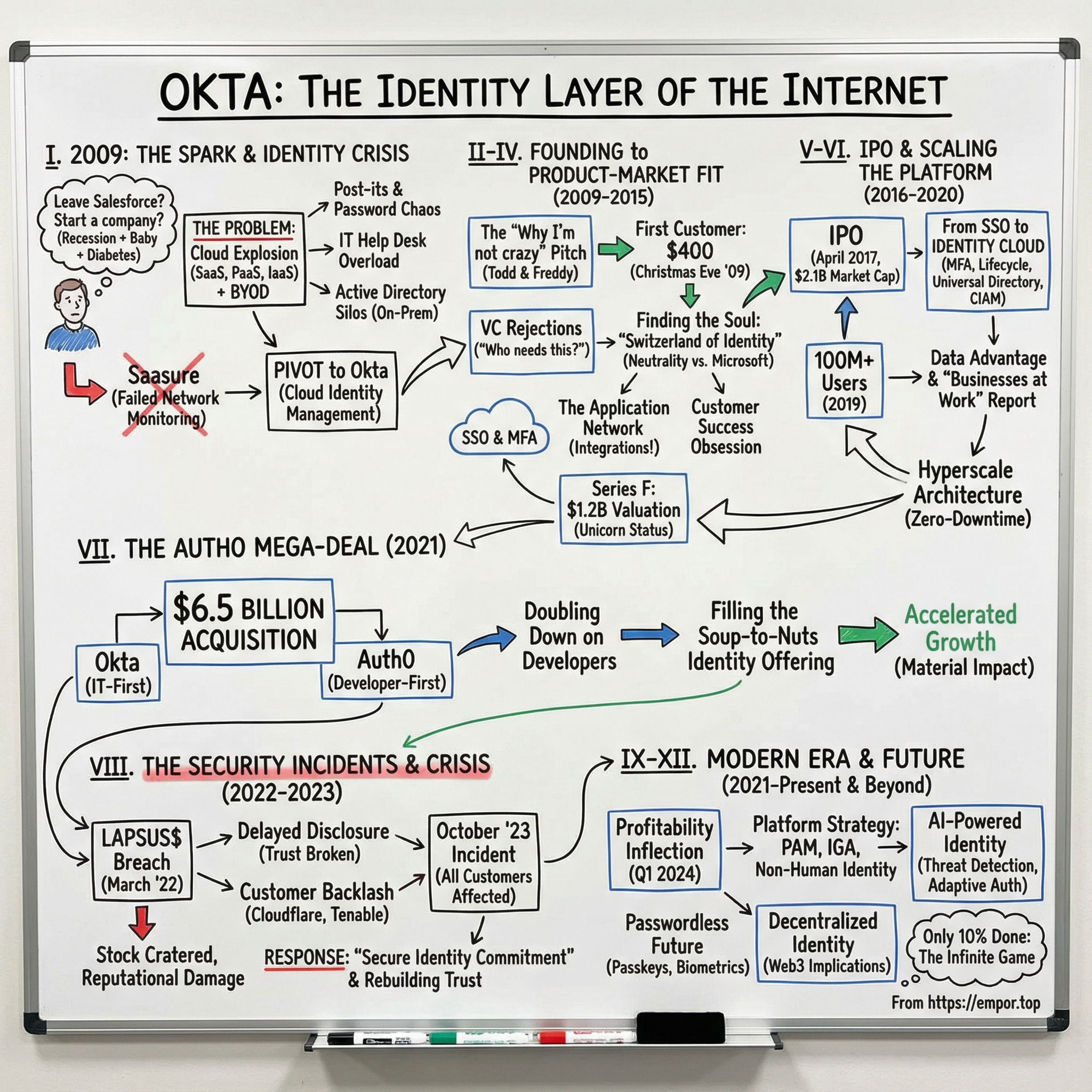
 Amazon Music
Amazon Music